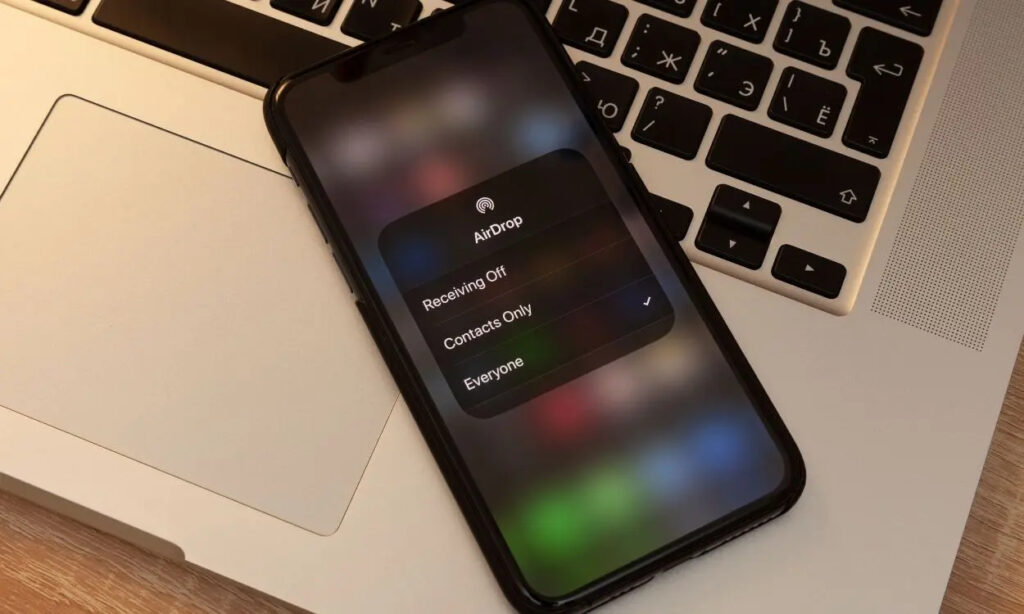
In a surprising development, the Chinese government has asserted that they have successfully breached Apple’s AirDrop security, claiming the ability to discern the phone numbers and email addresses of both senders and receivers. AirDrop is Apple’s exclusive file-sharing tool, facilitating the exchange of files among iOS and macOS users. Notably, the tool employs end-to-end encryption, displaying only the customized device names during transfers. This newly revealed method to circumvent the encryption directly violates Apple’s established policies.
According to a report from Bloomberg, China’s Judicial Bureau posted online, revealing that The Beijing Institute has formulated a technique enabling the extraction of AirDrop transfer records, ultimately allowing for the tracking of sender and receiver details. The motivation behind China’s focus on AirDrop stems from the prevalent misuse of the tool in the country, with individuals frequently employing it to share inappropriate videos and photos, particularly in public spaces like the Beijing Subway.
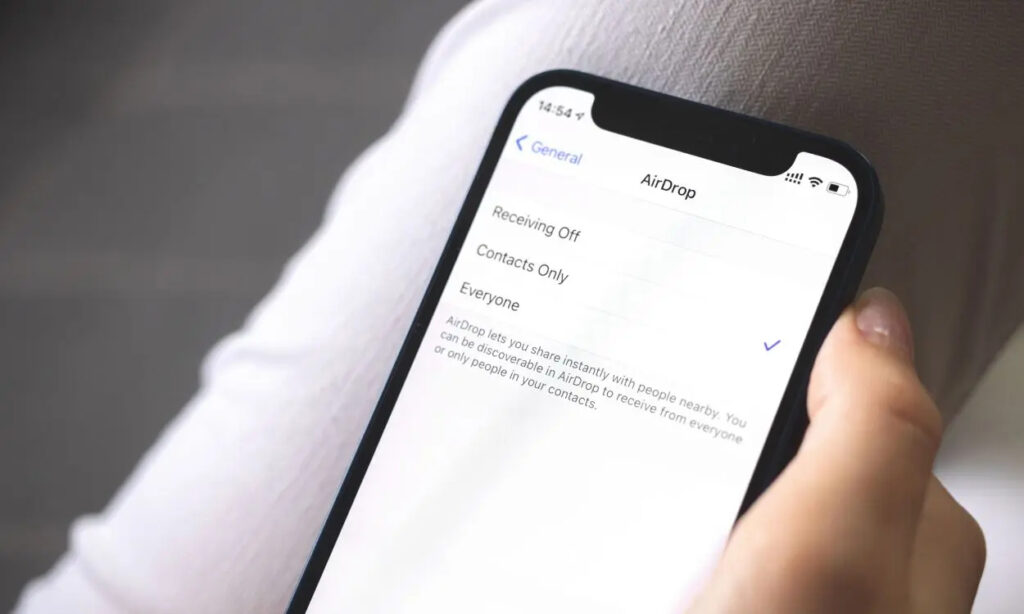
In a recent update to iOS 17, Apple introduced a groundbreaking feature that enables AirDrop file sharing even without an internet connection, rendering contemporary monitoring methods ineffective.
According to an online post by the Chinese Judicial Bureau, forensic technical experts from the Beijing Wangshendongjian Forensic Identification Institute conducted an analysis of iPhone device logs. Their findings revealed that the sender’s device name, email address, and mobile phone number were logged in the form of hash values. Notably, some of these hashed values were concealed, adding an extra layer of complexity to the tracking process.
To breach AirDrop encryption, the experts employed a “rainbow table,” a comprehensive database containing mobile phone numbers and email accounts that can convert hashed values back into their original text.
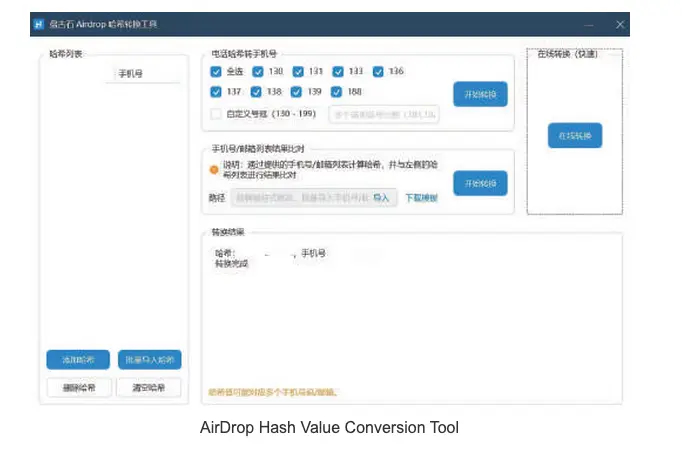
For those unfamiliar, the Rainbow Table attack is a password-hacking method that relies on a vast database of hash values associated with commonly used passwords. In this case, the hashed passwords extracted from iPhone logs were cross-referenced with a precomputed table of hashed passwords. This approach simplifies the decryption process, making it easier to unveil the original content from the hashed values.
Utilizing this method, law enforcement has successfully identified numerous suspected users who were employing AirDrop for sharing inappropriate videos and photos. The Beijing police, however, have not officially confirmed any arrests made in connection with the AirDrop case.
In response to multiple complaints about AirDrop misuse in China, Apple took action by incorporating an option to default AirDrop functionality to Contacts and introducing a “Everyone for 10 Minutes” setting.
As of now, Apple has not issued any statements regarding the situation and has yet to acknowledge China’s claim of a “technological breakthrough” in cracking AirDrop encryption.
0 Comments